- A group of six North Korean operatives using fake identities to get jobs with unwitting crypto projects has been revealed to be responsible for a US$680,000 June theft from Web3 ‘fan economy’ platform Favrr.
- The revelation came after an anonymous hacker was able to infiltrate one of the operatives’ devices, subsequently sharing his haul of incriminating evidence with crypto sleuth ZachXBT.
- One of the North Korean operatives had been hired as Favrr’s CTO, while several other operatives filled more junior roles at the project.
A group of six North Korean operatives using at least 31 fake identities to gain developer jobs at unsuspecting crypto companies has been exposed as the culprits behind a US$680,000 (AU$1m) June heist on the crypto ‘fan economy’ platform Favrr.
The group was exposed after an anonymous hacker was able to gain access to one of the group members’ devices, showing the group made heavy use of Google products and revealing the group’s infiltration tactics.
The anonymous hacker exported North Korean operatives’ Google Drive data and Chrome profiles along with a treasure trove of screenshots. This data was then shared with well-known crypto sleuth ZachXBT, who subsequently made it public through his X account.
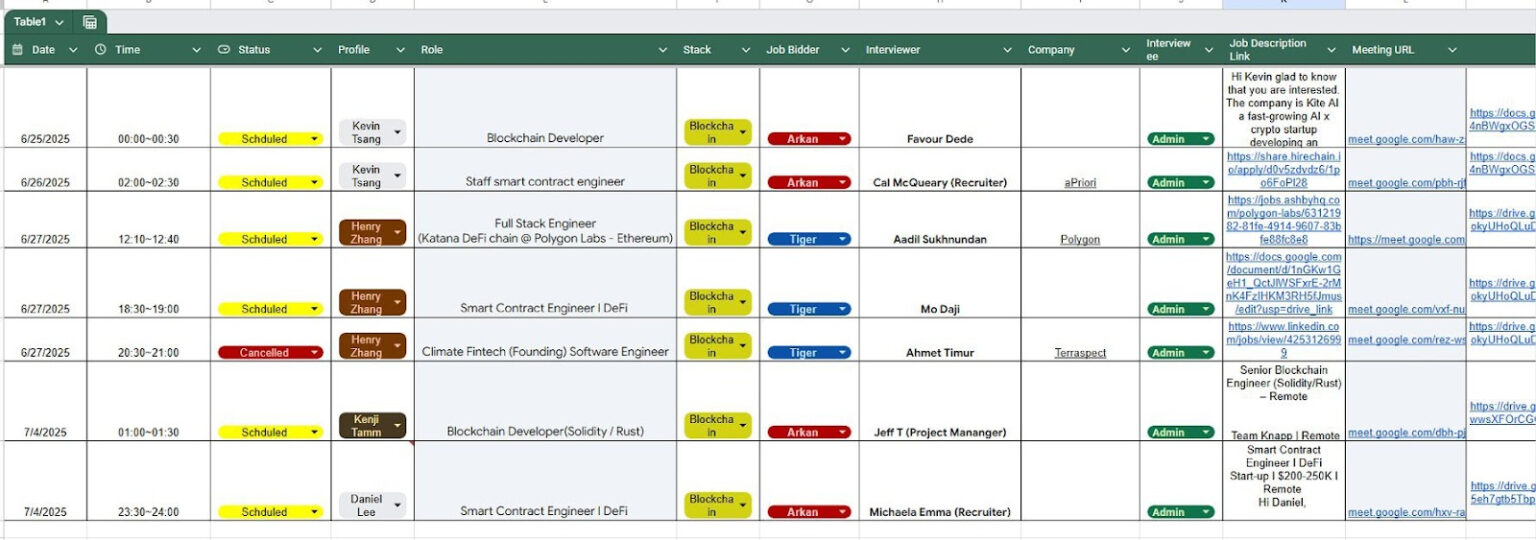
The information revealed that the members of the group had been able to acquire fraudulent government-issued identification documents and phone numbers for their 31 fake identities. They were also able to get LinkedIn profiles and accounts on freelance marketplaces like UpWork, allowing them to mask their true identities and get jobs with ostensibly legitimate crypto projects.
The group used tactics such as renting or buying computers, which they would then access remotely using AnyDesk through proxies and VPNs to hide their real locations. Once employed by unwitting crypto projects, such as Favrr, the operatives could then set about their nefarious work, stealing funds.
Shockingly, one of the documents shared by ZachXBT showed that a member of the hacking group had interviewed for a full-stack developer position at Polygon Labs, the primary developer behind the Ethereum side-chain Polygon.
Another document showed scripted interview responses claiming the North Korean operative had experience at leading NFT marketplace OpenSea and blockchain oracle provider Chainlink.
Related: North Korean Hackers Exploit Unusual “NimDoor” Malware to Breach Macs
One China Sleuthing Shows Group’s Wallet Linked to Favrr Heist
The information supplied to ZachXBT revealed an Ethereum address the operatives would often use to send funds to and from each other. As it turns out, this same address was also closely linked to the June hack on Favrr.
Unfortunately for Favrr, the person the company hired to fill the role of Chief Technical Officer (CTO), a man known as Alex Hong, was in fact a North Korean operative — as were several of their other employees. Hong and the other dodgy employees used the Ethereum address to embezzle the US$680,000 of funds out of Favrr, likely sending them back to the North Korean regime.
Related: FBI: Crypto Fraud Cases Increase by 45%, Reaching $5.6 Billion
A number of other crypto thefts have also been linked to the same group which hit Favrr — most notably multiple projects linked to Matt Furie, creator of the memecoin $PEPE, have had funds stolen by this same small group of North Korean operatives after hiring members to fulfil development roles.
The post North Korean Operatives Exposed in $680K Crypto Heist on Favrr appeared first on Crypto News Australia.